Raspberry Pi Tunnel: The Ultimate Guide To Secure And Efficient Networking
Raspberry Pi tunnel has become a popular solution for users looking to enhance their network security and privacy. Whether you're a tech enthusiast or a professional network administrator, understanding how Raspberry Pi tunnels work can help you create a more secure digital environment. In this article, we will explore the concept, applications, and benefits of Raspberry Pi tunnels while providing practical guidance for implementation.
Raspberry Pi, a small yet powerful device, has revolutionized the way people approach computing and networking. By leveraging its capabilities, users can set up secure tunnels to protect sensitive data and bypass geographical restrictions. In today's digital age, where cybersecurity threats are on the rise, understanding how to implement Raspberry Pi tunnels is crucial.
This comprehensive guide will walk you through the basics of Raspberry Pi tunnels, including their setup, configuration, and optimization. Whether you're setting up a personal tunnel for privacy or deploying an enterprise-grade solution, this article will provide you with all the information you need to succeed. Let's dive in!
Read also:All Lebron James Sneakers The Ultimate Guide For Collectors And Enthusiasts
Table of Contents
- Introduction to Raspberry Pi Tunnel
- A Brief History of Raspberry Pi Tunnels
- Types of Raspberry Pi Tunnels
- How to Set Up a Raspberry Pi Tunnel
- Security Benefits of Raspberry Pi Tunnels
- Performance Optimization for Raspberry Pi Tunnels
- Applications of Raspberry Pi Tunnels
- Troubleshooting Common Issues
- Raspberry Pi Tunnel vs. Traditional Solutions
- The Future of Raspberry Pi Tunnels
- Conclusion
Introduction to Raspberry Pi Tunnel
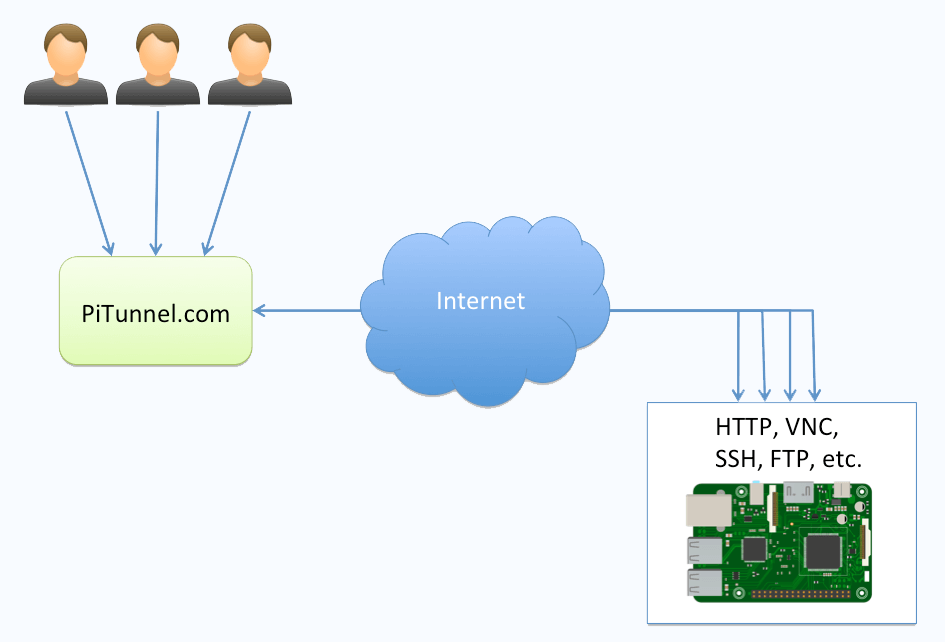
Raspberry Pi tunnel refers to the process of using a Raspberry Pi device to create a secure and encrypted connection between two networks or devices. This setup allows users to bypass censorship, enhance privacy, and securely access remote resources. The Raspberry Pi, known for its affordability and versatility, is ideal for such applications.
One of the key advantages of Raspberry Pi tunnels is their ability to provide robust security features without requiring expensive hardware. By leveraging open-source software and a lightweight architecture, Raspberry Pi tunnels can be deployed in various environments, from home networks to enterprise systems.
In this section, we will explore the fundamental principles behind Raspberry Pi tunnels and why they have gained popularity in recent years. Understanding these basics will lay the foundation for more advanced configurations later in the article.
A Brief History of Raspberry Pi Tunnels
The concept of network tunnels is not new, but the integration of Raspberry Pi into this domain has revolutionized the field. Initially developed as an educational tool, the Raspberry Pi quickly gained traction among hobbyists and professionals alike due to its flexibility and affordability.
As cybersecurity became a growing concern, developers began experimenting with Raspberry Pi for secure tunneling. This led to the creation of various tools and applications that enhanced the device's capabilities. Today, Raspberry Pi tunnels are widely used in both personal and professional settings, offering a cost-effective solution for secure networking.
Evolution of Raspberry Pi Tunnels
The evolution of Raspberry Pi tunnels can be traced back to the early days of the device's release. Initially, users relied on basic SSH tunnels for secure communication. Over time, more advanced protocols and configurations were introduced, allowing for greater flexibility and security.
Read also:Understanding The Role Of Computer At Websnapchatcom A Comprehensive Guide
Types of Raspberry Pi Tunnels
There are several types of Raspberry Pi tunnels, each designed to address specific use cases and requirements. Below are some of the most common types:
- SSH Tunnel: A simple and widely used method for creating secure connections between devices.
- OpenVPN Tunnel: A more advanced solution that offers greater flexibility and security features.
- IPSec Tunnel: Ideal for enterprise-grade applications requiring high levels of encryption and authentication.
- WireGuard Tunnel: A modern and lightweight protocol gaining popularity due to its simplicity and performance.
Choosing the Right Tunnel Type
Selecting the appropriate type of Raspberry Pi tunnel depends on factors such as the intended use, security requirements, and available resources. For example, SSH tunnels are suitable for basic needs, while OpenVPN or WireGuard may be better suited for more complex setups.
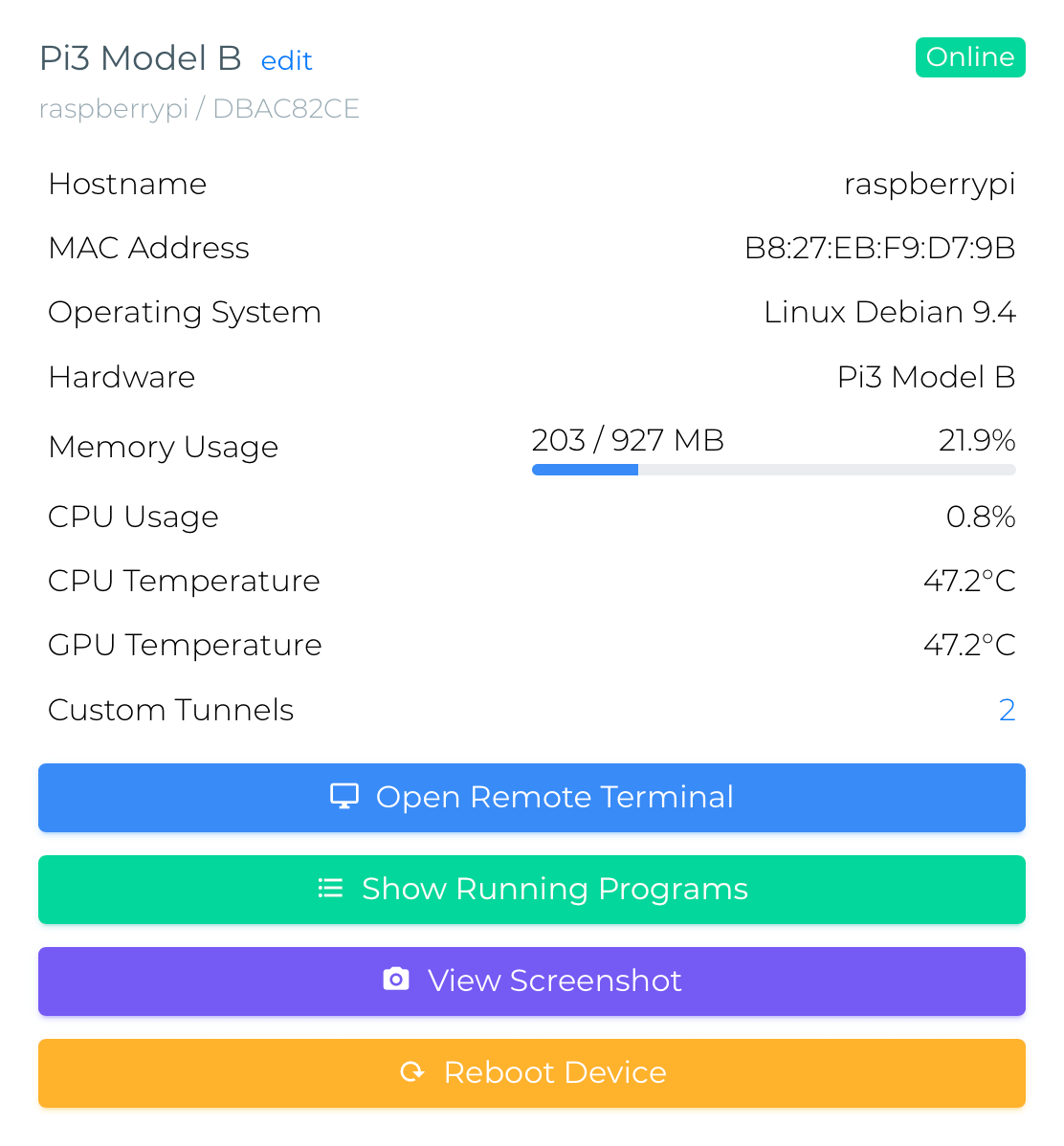
How to Set Up a Raspberry Pi Tunnel
Setting up a Raspberry Pi tunnel involves several steps, including hardware preparation, software installation, and configuration. Below is a step-by-step guide to help you get started:
- Install the latest version of Raspberry Pi OS on your device.
- Connect your Raspberry Pi to a stable power source and network.
- Install the necessary software, such as OpenVPN or WireGuard, depending on your chosen tunnel type.
- Configure the tunnel settings, including encryption protocols and authentication methods.
- Test the connection to ensure everything is working as expected.
Advanced Configuration Tips
For users seeking more advanced configurations, consider implementing features such as split tunneling, firewall rules, and automated scripts to enhance performance and security.
Security Benefits of Raspberry Pi Tunnels
Raspberry Pi tunnels offer numerous security benefits, making them an attractive option for users concerned about data privacy. Some of the key advantages include:
- Encryption: All data transmitted through a Raspberry Pi tunnel is encrypted, ensuring that sensitive information remains secure.
- Authentication: Tunnels can be configured to require strong authentication methods, reducing the risk of unauthorized access.
- Geo-Blocking Bypass: Users can bypass geographical restrictions by routing their traffic through a Raspberry Pi tunnel located in a different region.
Best Practices for Security
To maximize the security benefits of Raspberry Pi tunnels, follow these best practices:
- Regularly update your Raspberry Pi OS and installed software to address potential vulnerabilities.
- Use strong passwords and consider implementing multi-factor authentication.
- Monitor your tunnel's activity for any suspicious behavior.
Performance Optimization for Raspberry Pi Tunnels
While Raspberry Pi tunnels are highly secure, they can sometimes impact network performance. To optimize performance, consider the following tips:
- Choose the right tunnel type based on your specific needs and available resources.
- Optimize encryption protocols to strike a balance between security and speed.
- Use quality-of-service (QoS) settings to prioritize critical traffic.
Troubleshooting Performance Issues
If you encounter performance issues with your Raspberry Pi tunnel, try the following troubleshooting steps:
- Check your network connection for stability and bandwidth limitations.
- Verify that your Raspberry Pi is running the latest firmware and software updates.
- Adjust tunnel settings to improve efficiency and reduce latency.
Applications of Raspberry Pi Tunnels
Raspberry Pi tunnels have a wide range of applications, spanning both personal and professional use cases. Some common applications include:
- Personal Privacy: Users can protect their online activities from prying eyes by routing traffic through a Raspberry Pi tunnel.
- Remote Access: Businesses can securely access remote resources by deploying Raspberry Pi tunnels in their network infrastructure.
- IoT Security: Raspberry Pi tunnels can enhance the security of IoT devices by encrypting their communication channels.
Real-World Examples
Many organizations and individuals have successfully implemented Raspberry Pi tunnels to address their unique needs. For instance, a small business might use a Raspberry Pi tunnel to securely connect multiple branch offices, while a homeowner could use it to protect their smart home devices.
Troubleshooting Common Issues
Like any technology, Raspberry Pi tunnels can encounter issues that need to be addressed. Below are some common problems and their solutions:
- Connection Failures: Verify that all settings are correctly configured and that the Raspberry Pi is properly connected to the network.
- Performance Degradation: Optimize tunnel settings and monitor network traffic for bottlenecks.
- Security Breaches: Regularly update software and implement strong authentication methods to prevent unauthorized access.
When to Seek Professional Help
If you encounter persistent issues or lack the expertise to resolve them, consider consulting a professional with experience in Raspberry Pi tunnels. They can provide tailored solutions to address your specific challenges.
Raspberry Pi Tunnel vs. Traditional Solutions
While Raspberry Pi tunnels offer numerous advantages, they may not be the best solution for every situation. Below is a comparison of Raspberry Pi tunnels with traditional networking solutions:
| Criteria | Raspberry Pi Tunnel | Traditional Solutions |
|---|---|---|
| Cost | Low | High |
| Flexibility | High | Moderate |
| Scalability | Moderate | High |
Choosing the Right Solution
When deciding between a Raspberry Pi tunnel and a traditional solution, consider factors such as budget, scalability, and technical expertise. Raspberry Pi tunnels are ideal for cost-conscious users who require flexibility, while traditional solutions may be better suited for large-scale deployments.
The Future of Raspberry Pi Tunnels
As technology continues to evolve, so too will the capabilities of Raspberry Pi tunnels. Future advancements may include improved performance, enhanced security features, and greater integration with emerging technologies such as 5G and IoT. Staying informed about these developments will help users make the most of their Raspberry Pi tunnel setups.
Trends to Watch
Some trends to watch in the world of Raspberry Pi tunnels include the adoption of new encryption standards, increased automation, and tighter integration with cloud services. These advancements promise to make Raspberry Pi tunnels even more powerful and versatile in the years to come.
Conclusion
Raspberry Pi tunnels represent a cost-effective and flexible solution for enhancing network security and privacy. By understanding their principles, applications, and configurations, users can leverage this technology to meet their unique needs. Whether you're setting up a personal tunnel for privacy or deploying an enterprise-grade solution, Raspberry Pi tunnels offer a compelling option.
We encourage you to experiment with Raspberry Pi tunnels and explore their potential. Feel free to leave a comment below with any questions or feedback, and don't forget to share this article with others who may find it useful. For more information on Raspberry Pi and related topics, explore our other articles on the site.